A firewall acts as a security guard for your computer or network, managing the flow of data between your computer (or network) and the internet or other networks. It scrutinizes the data packets — small chunks of data — to determine whether they should be allowed through or not, based on a set of security rules.

Imagine your computer as your home. Just as you would have a door to control who comes in and out, a firewall performs a similar function for your computer or network. It decides which data packets can enter or leave, akin to deciding who can enter or exit your home.
For example, if you’re browsing the internet and clicking on various websites, your firewall evaluates the incoming data from these sites to ensure they’re not harmful or unsolicited. If you receive an email with an attachment, the firewall reviews the attachment to confirm it doesn’t contain any malware that could harm your computer. It’s like having a security checkpoint that checks IDs (data packets) against a guest list (security rules). If the ID matches the guest list, entry is granted; if not, access is denied, keeping your digital space secure.
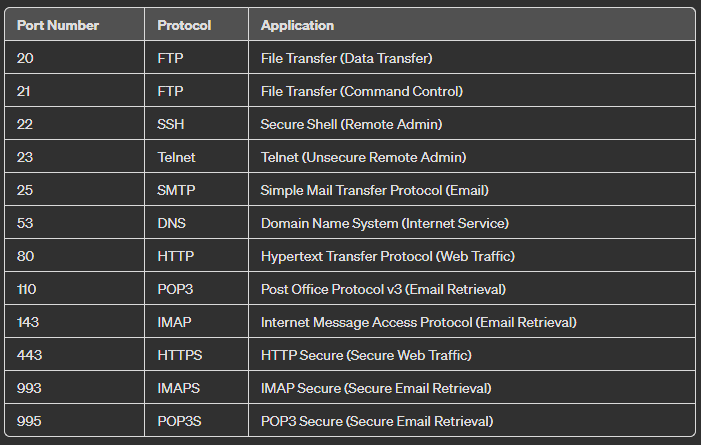
A firewall also sorts data using ports and protocols, which can be likened to the various doors and rules of entry into a building. Each type of service on the internet communicates through specific ports, which are like different doors designated for specific purposes. Protocols, on the other hand, are the set of rules or customs for transmitting data. They ensure that data sent over the internet is packaged and delivered in a way that the receiving system can understand and use.
For example, think of your computer as a large office building, with each room (port) designated for a specific type of communication or service. The mail room might use one door (port) for receiving parcels (emails), while the loading dock uses another door (port) for large deliveries (file transfers). The rules for how parcels are packaged, addressed, and delivered (protocols) ensure that they reach the correct room efficiently and are understood by the recipient.
When data tries to enter or leave your network, the firewall checks the port number (the door it’s trying to use) and the protocol (the rules it’s following) to decide if this data should be allowed. If data is attempting to use a port that’s not expected or is not following the right protocol rules, the firewall can block it. For instance, if someone tries to send email data through the port typically used for web browsing, the firewall might block it because it doesn’t follow the expected pattern of legitimate traffic, akin to someone trying to deliver a pizza to the mail room—it just doesn’t fit the established norms, so the security guard (firewall) steps in to prevent potential chaos or harm.