RSA (Rivest-Shamir-Adleman) Description
RSA is a widely-used public-key cryptographic algorithm named after its creators, Ron Rivest, Adi Shamir, and Leonard Adleman. Introduced in 1977, RSA is one of the first and most prevalent public-key cryptosystems. It’s based on the mathematical challenge of factoring the product of two large prime numbers, which forms the basis of its encryption and decryption processes.
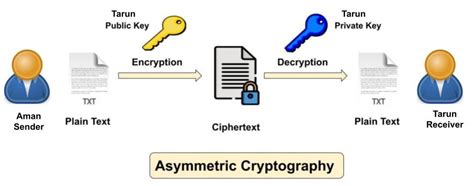
Image of RSA Cryptography from Public-key-cryptography-1.jpg (992×391) (cybermeteoroid.com)
In RSA, the encryption key is public and differs from the decryption key which is kept private. This asymmetry is what makes RSA a public-key (or asymmetric) cryptography system.
Basic Use of RSA
- Secure Data Transmission: RSA is used for securing data transmission over the internet. It encrypts sensitive information with a public key, which can only be decrypted with the corresponding private key, ensuring that only the intended recipient can access the original data.
- Digital Signatures: RSA is also used to create digital signatures. A sender can encrypt data (typically a hash of the message) with their private key. The recipient, or any third party, can then use the sender’s public key to decrypt and verify the data, confirming the integrity of the message and the authenticity of the sender.
- SSL/TLS for Secure Web Browsing: In the SSL/TLS protocols, which secure communications over computer networks, RSA is often used for securely exchanging symmetric encryption keys at the start of a session. This ensures that the subsequent data transfer is encrypted and protected.
- Authentication: RSA enables the authentication of identities in digital communications, verifying that messages or transactions are not from imposters.
- Key Exchange: RSA facilitates the secure exchange of cryptographic keys in various network security applications, including VPNs and secure email.
Security and Computational Load
RSA’s security is rooted in the computational difficulty of factoring large prime numbers. However, this same factor also makes RSA computationally intensive compared to symmetric key algorithms. Therefore, it’s often used in combination with symmetric encryption – RSA to securely exchange keys and symmetric algorithms for efficient data encryption.
The continuing evolution of computing power, including the development of quantum computers, poses challenges to RSA’s security. As such, the cryptography community is actively researching post-quantum cryptographic methods.
Extra
Rivest-Shamir-Adleman.
RSA
Caesar Cipher Game
Enter a message to encode or decode:
Enter the Caesar cipher key:
