Project report, knowledge test, scenarios, professional discussion.
Assessment 01
Project Report Reminder
- The project report has a maximum word limit of 2,000 words. A tolerance of plus or minus 10% is allowed. Appendices, references, diagrams etc will not be included in this total. Where organisational documents are required, screenshots or extracts should be provided.
- Hyperlinks to external sources will not be permitted.
- All project reports (irrespective of the option chosen) should include:
- An introductory section (text only, i.e. no diagrams, screen shots or figures) that explains:
- description of the project
- approach
- project outcomes
- How the KSB are evidenced through the project
- You MUST include ALL criteria evidence to ensure you pass.
- Please triple check against your proposal of how you are going to approach each area and please send to your managers to overlook before submitting to EPA@estio.co.uk – Coaches/Trainers are not allowed to have any input once you enter gateway.
Project Report Checklist
-
Word Count
- The project report has a maximum word limit of 2,000 words.
- A tolerance of plus or minus 10% is allowed.
- Appendices, references, diagrams, etc., are not included in the total word count.
- Screenshots or extracts of organisational documents are provided where required.
-
Hyperlinks
- Hyperlinks to external sources are not included in the report.
-
Report Content
- The report includes an introductory section (text only, no diagrams, screenshots, or figures) that explains:
- Description of the project
- Approach
- Project outcomes
- How the KSB are evidenced through the project
- The report includes an introductory section (text only, no diagrams, screenshots, or figures) that explains:
-
Criteria Evidence
- All criteria evidence is included to ensure a pass.
- Triple-checked against the proposal to ensure all areas are approached correctly.
- Sent to managers for review before submission to EPA@estio.co.uk.
- Coaches/Trainers have not provided input once you have entered the gateway.
Pathways
Security Engineer Pathway
This 6 week project is to design, build, test, troubleshoot a network.
You can use packet tracer to develop the network or any other virtual network tool to complete this.
Headings to be used within project report:
For Cyber Security Engineer Option, the Project report must cover the following additional headings:
• design of the network
• evidence that the network works to meet the requirement
• network optimisation metrics against performance requirements
• requirements analysis and its link to the eventual system, including security features
• schematics to show the build of a system to the design from provided components
• configuration metrics to show how the system to meet the security requirements
• demonstration of how the security features are effective
Criteria to meet:
S10
PASS
Designs, builds tests and troubleshoots a network incorporating:
more than one subnet
with static and dynamic routes
that includes
- Servers
- Hubs
- Switches
- Routers
and user devices to a given design requirement without supervision.
DISTINCTON
Evaluates network performance with reference to the design requirements and identifies using troubleshooting techniques ways to implement improvements
S11
PASS
Analyses functional and non-functional security requirements presented in a security case against other design requirements identifying conflicts and justifying a solution based on valid trade-offs.
S12
PASS
Designs and builds, within broad but generally well-defined parameters, a system in accordance with a security case.
Including selection and configuration of typical security hardware and software components.
For example:
A system at the enterprise, network or application layer ensuring that the system has properly implemented security controls as required by the security case.
DISTINCTION
Analyse the rationale and consequences of the selection of typical security components for the business
S14
PASS
Designs a system employing encryption to meet defined security objectives and develops and implements a plan for managing the associated encryption keys for the given system.
DISTINCTION
Critically evaluate the use of encryption and the plan for the management of encryption keys in terms of the usability, costs and benefits for relevant stakeholders
Risk Analyst Pathway
This 6 week project is covering multiple different criteria within a Risk Analyst job role such as:
- Taking part in an audit & producing a gap analysis
- Producing a risk assessment of findings and including the standard/methodology used & risk matrix
- Creating/developing & showing amendments to a Policy & process from findings
- Creating a business continuity plan & assessing the security culture & implementing and designing a security awareness campaign.
Headings to be used within the project report:
For Cyber Risk Analyst Option, the Project Report must cover the following additional headings:
• description of the role taken in a cyber security risk assessment and audit
• a report explaining the conduct of the risk assessment & audit
• a report considering the cyber policies and cyber awareness campaign
Criteria to meet:
S16
PASS
Conducts a cyber-risk assessment against an externally (market) recognised cyber security standard using a recognised risk assessment methodology.
S18
PASS
Develops an information security policy or process to address identified risks for example from security audit recommendations
S19
PASS
Develops an information security policy within a defined scope to take account of relevant cyber security legislation and regulation
DISTINCTION
Analyses the rationale and consequences of the design of a typical information security policy for the business
S20
PASS
Implements part of a security audit against a recognised cyber security standard, undertake a gap analysis and makes recommendations for remediation
S22
PASS
Develops a local business continuity plan for approval within an organisations’ governance arrangements for business continuity
DISTINCTION
Analyses the rationale and consequences of the design of a typical business continuity plan for the business
S23
PASS
Assesses security culture using a recognised approach
S24
PASS
Designs and implements a simple ‘security awareness’ campaign to address a specific aspect of a security culture
DISTINCTION
Evaluates with evidence the outcomes from a security awareness campaign and propose improvements
Risk Analyst Pathway Help
Gap analysis
https://securityscorecard.com/blog/how-to-perform-an-information-security-gap-analysis/
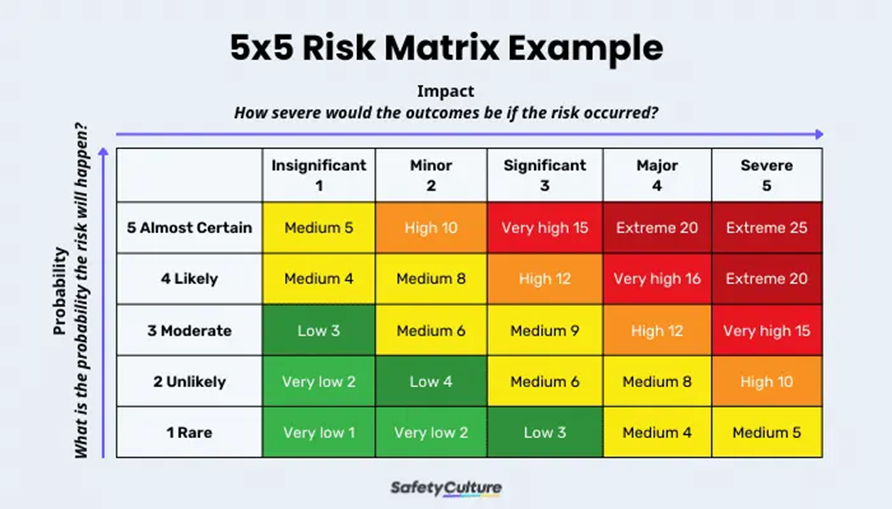
Risk Assessment: Standards/Methodology/Examples/Risk Matrix
– https://www.itgovernance.co.uk/iso27001/iso27001-risk-assessment
– https://www.itgovernance.co.uk/iso27005
– https://secureframe.com/blog/risk-management-methodologies
Risk Assessment Example
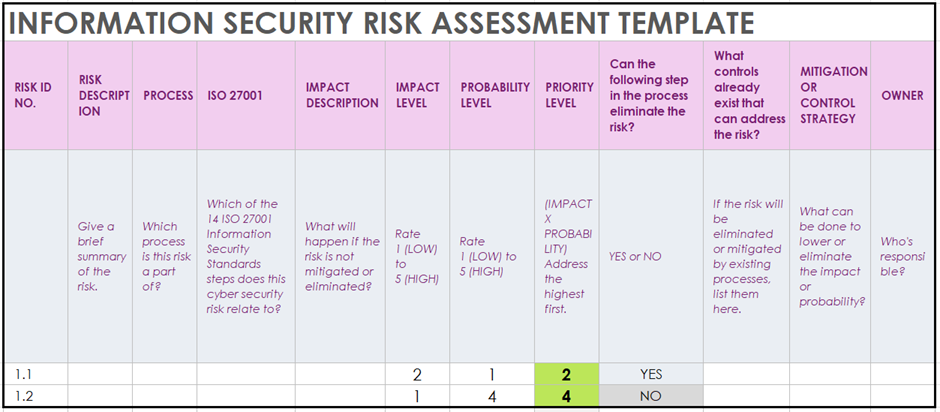
Risk Matrix Example
Policy
https://www.sans.org/information-security-policy/
Process
https://www.pipefy.com/blog/process-mapping/
Business Continuity Plan
https://www.itgovernance.co.uk/blog/how-to-create-a-business-continuity-plan-with-free-template
Security Awareness Campaign
https://www.hutsix.io/cyber-awareness-month-campaign-ideas-2023/
Assessing Security Culture – Survey Monkey, Microsoft Forms, Phishing Campaign.
Defend & Respond Pathway
This 6 week project is the investigation & analysing information from an array of information including SIEM Tools, Log Files etc to produce & incident response plan & configure a monitoring tool in relation to the investigation/threat/vulnerability intelligence.
Headings to be used within the project report:
For Cyber Security Defender and Responder Option the Project Report must cover the following additional headings:
• incident manager report of an incident response
• incident response plan submitted for approval
• detection of a security incident and action taken
• analysis of a security incident and action taken
• evidence of the implementation of tool configuration in response to threat intelligence
Criteria to meet
S21
PASS
Develops an incident response plan for approval within an organisations’ governance arrangements for incident response
DISTINCTION
Analyses the rationale and consequences of the design of a typical incident response plan for the employer, business, or organisation
S25
PASS
Integrates and correlates information from various sources (including log files from different sources, digital system monitoring tools, Secure Information and Event Management (SIEM) tools, access control systems, physical security systems) and compares organisational data to known threat and vulnerability data to form a judgement based on evidence with reasoning that the anomaly represents a digital system security breach
S26
PASS
Recognises anomalies in observed digital system data structures (including by inspection of network packet data structures) and digital system behaviours (including by inspection of protocol behaviours) and by inspection of log files and by investigation of alerts raised by automated tools including SIEM tools
S25 and S26
DISTINCTION
Evaluates how the recognised incidents demonstrate the threat actors’ approach i.e. what is going on that causes the observed anomalies and what the motive could be
S28
PASS
Configures digital system monitoring and analysis tools (e.g. SIEM tools), taking account of threat & vulnerability intelligence, indicators of compromise
DISTINCTION
Analyses the rationale and consequences of selecting and configuring digital system monitoring tools for the employer, business, or organisation
S29
PASS
Undertakes root cause analysis of events and makes recommendations to reduce false positives and false negatives.
S30
PASS
Manages local response to non-major incidents in accordance with a defined procedure
Defend & Respond Pathway Help
Anomaly Detection Explained
https://www.xenonstack.com/insights/cyber-network-security
Incident response plan
https://www.bluevoyant.com/knowledge-center/top-8-incident-response-plan-templates
