RSA
RSA (Rivest-Shamir-Adleman) Description
RSA is a widely-used public-key cryptographic algorithm named after its creators, Ron Rivest, Adi Shamir, and Leonard Adleman. Introduced in 1977, RSA is one of the first and most prevalent public-key cryptosystems. It’s based on the mathematical challenge of factoring the product of two large prime numbers, which forms the basis of its encryption and decryption processes.
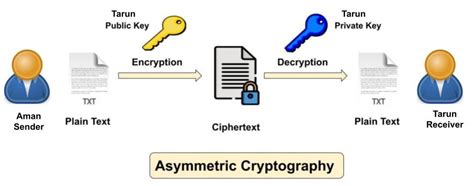
Image of RSA Cryptography from Public-key-cryptography-1.jpg (992×391) (cybermeteoroid.com)
In RSA, the encryption key is public and differs from the decryption key which is kept private. This asymmetry is what makes RSA a public-key (or asymmetric) cryptography system.
Basic Use of RSA
- Secure Data Transmission: RSA is used for securing data transmission over the internet. It encrypts sensitive information with a public key, which can only be decrypted with the corresponding private key, ensuring that only the intended recipient can access the original data.
- Digital Signatures: RSA is also used to create digital signatures. A sender can encrypt data (typically a hash of the message) with their private key. The recipient, or any third party, can then use the sender’s public key to decrypt and verify the data, confirming the integrity of the message and the authenticity of the sender.
- SSL/TLS for Secure Web Browsing: In the SSL/TLS protocols, which secure communications over computer networks, RSA is often used for securely exchanging symmetric encryption keys at the start of a session. This ensures that the subsequent data transfer is encrypted and protected.
- Authentication: RSA enables the authentication of identities in digital communications, verifying that messages or transactions are not from imposters.
- Key Exchange: RSA facilitates the secure exchange of cryptographic keys in various network security applications, including VPNs and secure email.
Security and Computational Load
RSA’s security is rooted in the computational difficulty of factoring large prime numbers. However, this same factor also makes RSA computationally intensive compared to symmetric key algorithms. Therefore, it’s often used in combination with symmetric encryption – RSA to securely exchange keys and symmetric algorithms for efficient data encryption.
The continuing evolution of computing power, including the development of quantum computers, poses challenges to RSA’s security. As such, the cryptography community is actively researching post-quantum cryptographic methods.
Extra
Rivest-Shamir-Adleman.
RSA
RSA (Rivest-Shamir-Adleman) is a widely used asymmetric encryption algorithm that is based on the mathematical principles of modular arithmetic and the difficulty of factoring large prime numbers. It involves a key pair consisting of a public key and a private key, where the public key is used for encryption and the private key is used for decryption.
Here’s a step-by-step example of how RSA encryption and decryption work:
Key Generation:
- Select two distinct prime numbers, p and q. For example, let’s say p = 17 and q = 11.
- Compute n = p * q. In this case, n = 17 * 11 = 187.
- Compute Euler’s totient function, φ(n), which is the number of positive integers less than n that are coprime to n. For RSA, φ(n) = (p – 1) * (q – 1) = 16 * 10 = 160.
- Choose an integer e such that 1 < e < φ(n) and e is coprime to φ(n). In this example, let e = 7.
- Calculate the private key, d, such that (e * d) % φ(n) = 1. In this case, d = 23.
Encryption:
- Convert the plaintext message into a numerical representation. For example, if the message is HELLO, it can be represented as 0725 (using ASCII codes).
- Apply the encryption formula: ciphertext = (plaintext^e) % n. Using the values above, the ciphertext is calculated as (0725^7) % 187 = 75.
Decryption:
- Take the ciphertext and apply the decryption formula: plaintext = (ciphertext^d) % n. Using the values above, the plaintext is calculated as (75^23) % 187 = 0725.
- Convert the numerical representation back into the original plaintext message. In this case, 0725 corresponds to HELLO.
In RSA, the security of the encryption relies on the difficulty of factoring large numbers. The private key, which is required for decryption, must be kept secret, while the public key can be freely shared. Anyone with the public key can encrypt messages, but only the holder of the private key can decrypt them.
It’s worth noting that RSA is a complex algorithm with many additional considerations, such as padding schemes and key size selection, to ensure security and prevent attacks. The example provided here is a simplified illustration of the basic steps involved in RSA encryption and decryption.
Caesar Cipher Game
Enter a message to encode or decode:
Enter the Caesar cipher key:
